
When developing financial apps you probably get the requirement to detect jailbroken devices. The reason for detection is to either disable some or most of the app’s functionalities due to security concerns that come from a jailbroken system.
This article is discussing why jailbreak detection is useless – in most cases.
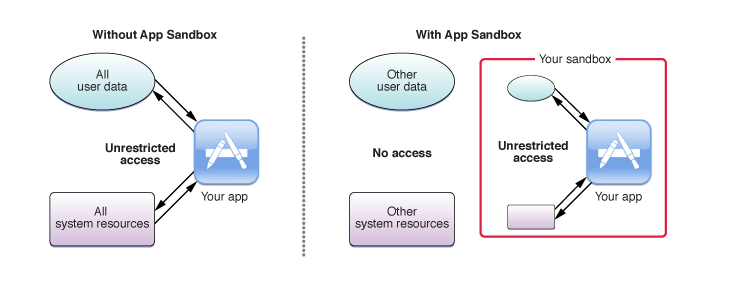
What is sandboxing?
Every app runs inside a sandbox of its own. This means that every app has very limited access to system resources like filesystem, memory, user data hardware or other app data. If an iOS apps needs to access information or resources it always declares this in its entitlement. Since entitlements are digitally signed they can not be changed and the app resource data ownership can be assured by the operating system.
While App Sandbox doesn’t prevent attacks against your app, it does minimize the harm a successful one can cause.
What is a jailbreak?
Imagine that sandbox is a kind of a jail for your app. In this sense the term jailbreak means that your iOS app can get resources outside of it’s jail. In other words jailbreaking gives the apps admin (root) level access. It allows to install other apps not in App Store and/or tweaked Apps and these apps can access resources as they like.
Most of the jailbroken devices use Cydia – the unofficial official jailbreak software manager.
Apple views jailbreaking as a violation of the End-user license agreement, and strongly cautions device owners from attempting to achieve root access through exploitation of vulnerabilities.
However when a user is jailbreaking his own device he is not only violating the law but he is also giving up his own security – as sandboxing is not assured by the operating system. Installed apps on a jailbroken device can access each others data!
So a reasonable Apple iOS user will not jailbreak his device… Never ever!
Breaking the jailbreak
So, now that we’re familiar with what jailbreaking is, it’s time to discuss how developers detect a jailbreak. While there’s no official way to detect a jailbreak, and false positives are possible, most methods rely on attempts to access resources that are usually inaccesible on a sandboxed app.
So, now that we’re familiar with what jailbreaking is, it’s time to discuss how developers detect a jailbreak. While there’s no official way to detect a jailbreak, and false positives are possible, most methods rely on attempts to access resources that are usually inaccesible on a sandboxed app. For example we will try to
- Try to find the presence of Cydia
- Attempt to find existence of CydiaSubstrate, the framework that allows installation of third-party patches
- Attempt to access directories that should not be available to an app without escalated privileges
- Try to find symbolic links to usually unavailable directories or, attempt to write to a directory where that usually wouldn’t be possible
While companies started to secure their apps against jailbreaking with the above methods hackers started to remove jailbreaking mechanisms with tweaks. And trust me removing jailbreak detection is easy and just a step further along the street. There is even a guide how todo this on Cydia.
There are even Apps to break the jailbreak detection of global payment apps like Paypal – PalBreak.
The solution is to inform your customers not to use your banking or payment App on a jailbroken device as there is the risk they will loose their money. Most of them will know anyway.
Conclusion
While jailbreak detects indeed may, at first glance, give more security to payment apps, they don’t contribute too much to App security, since they can be targeted and disabled and might just alienate minor part of advanced invaders.
However most of iOS user base is aware of the security concerns a jailbreak presents to them and they won’t do it.
User Awarness and Information is always better then a technical solution that pretends security.
